![]() The Mosquitto MQTT broker can be configured to require client authentication using a valid username and password before a connection is permitted.
The Mosquitto MQTT broker can be configured to require client authentication using a valid username and password before a connection is permitted.
The username and password combination is transmitted in clear text, and is not secure without some form of transport encryption.(SSL)
However using username and password authentication does provide an easy way of restricting access to a broker.
Note: The username used for authentication can also be used in restricting access to topics.
In this tutorial we look at how to configure username and password restrictions on the mosquitto broker, and look how it works by looking at some connection examples using simple Python test scripts.
Mosquitto Broker Configuration
All forms of restrictions i.e. client id, username/password, topic etc are implemented on the MQTT broker.
Once implemented on the broker it is up to the client to comply with these restrictions in order to connect, subscribe and publish.
To configure the Mosquitto broker you will need to:
- Create a password file
- Edit the mosquitto.conf file to force password use.
To create a password file you need to use the mosquitto_passwd utility that comes with the client tools when installing the mosquitto broker.
There are several ways of doing this:
Method 1
Create a simple text file and enter the username and passwords, one for each line, with the username and password separated by a colon as shown below.
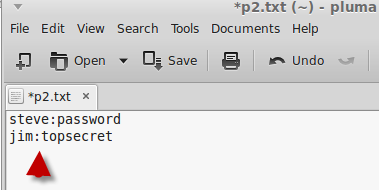
Close the file in the text editor.
Now you need to convert the password file which encrypts the passwords, Go to a command line and type:
Now if you open the password file again you should see this:
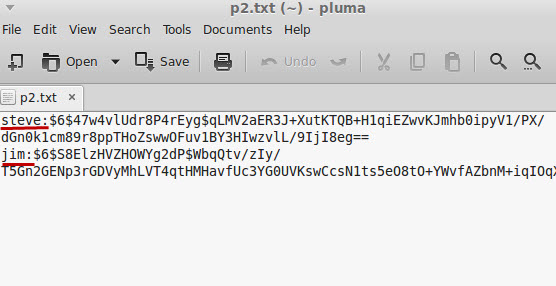
The passwords file is now ready to use.
Method 2
You create the password file using the command
Note you need to enter a username for this to work. This adds the user to the password file.
You will be prompted to enter a password for the user.
Now you can use the command
to add additional users to the file.
The screenshot below shows the process:
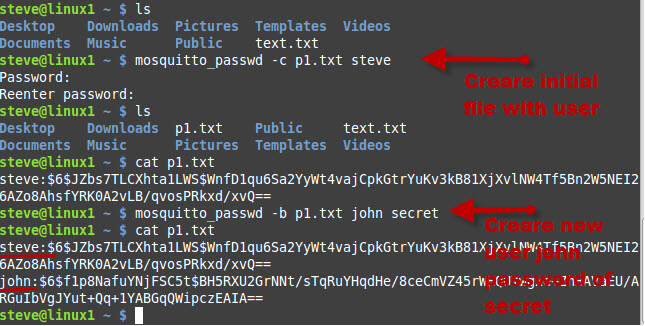
You can also delete users from the password file using the command
Important Note: The mosquitto_passwd utility did not work on my Windows XP installation, and I had to use the utility on my Linux installation.
However it did work on windows 7 and 10 but I needed to add the msvcr100.dll file. See Installing the Mosquitto Broker-client scripts
Using the Password file
You will need to copy the password file into the etc\mosquitto folder ( linux ) or the mosquitto folder(windows) and then edit the mosquitto.conf file to use it.
The two changes you normally make in the mosquiito.conf file are to set allow anonymous to false and to set the password_file path.
It should be noted that since mosquitto v1.5 authentication is no longer a global setting but can be configured on a per listener basis.
However this must be enabled using the per_listener_settings setting at the top of the file.
To enable it use:
per_listener_settings true
mosquitto.conf- Example Settings
allow_anonymous false
password_file c:\mosquitto\passwords.txt #Windows machine
Example Password File
An Example password file called pwfile.example is provided with the installation.
The file has three users:
- roger
- sub_client and
- pub_client.
All three users have a password of password.
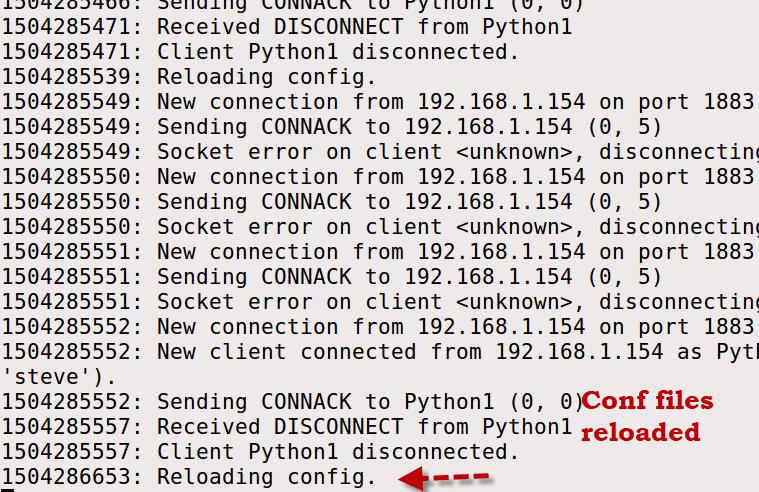
Reloading the Password File
If you make a change to the configuration files including the password file you can restart the mosquitto broker.
However on Linux you can reload the configuration files without restarting the broker by using the following:
kill-HUP PID # where PID is the process ID as shown below:
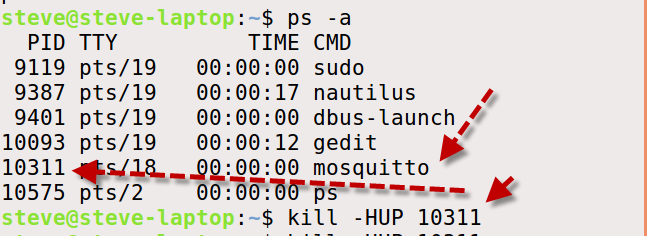
If you look at the console it should show that the conf files have been reloaded
Paho Python MQTT Client Configuration
To connect to a broker that implements username/password restrictions you need to use the helper method username_pw_set() of the Paho client.
This you must call before establishing the connection.
The format is:
Detecting Authentication Errors
If you try to connect to a broker without the correct authentications details the connection will be rejected.
To detect this you will need to examine the on_connect callback.
If you examine the documentation for the on_connect callback method you will see that it accepts 4 parameters.
The rc parameter is the return code and should be 0 for a good connection.
A return code of 5 indicates an authentication error.
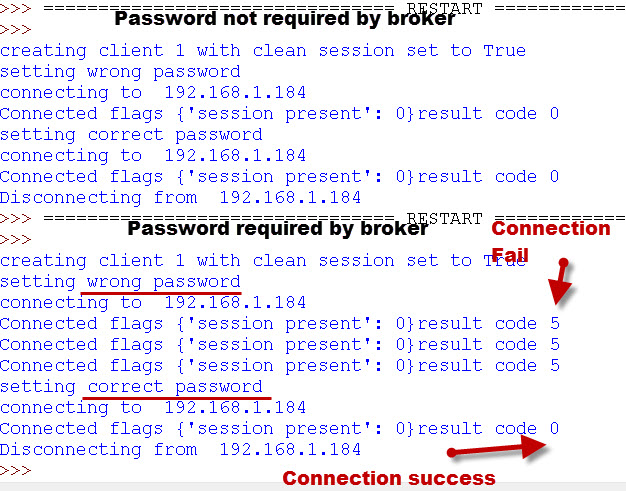
Password Connection Examples:
The screen shots below show the results of connecting a client to a broker with incorrect and correct passwords.
The on_connect callback method shown below just prints out the return code and looks like this:
def on_connect(client, userdata, flags, rc):
print("Connected flags ",str(flags),"result code ",str(rc))[/outline]
Example 1– In the first attempt the broker isn’t configured to require passwords, and so it simply ignores the wrong password.
Example 2– In the second connection attempt the broker is configured to require a username and password, and rejects the connection attempt with the bad password.
When Using MQTTv5 a return string of Not Authorised is returned and the actual code is 135.

Broker Access Control Explained
For username/password control to work correctly then there are two settings that need to be configured on the broker.
They are:
- allow_anonymous and
- password_file.
Example:
allow_anonymous false
password_file c:\mosquitto\passwords.txt #Windows machine
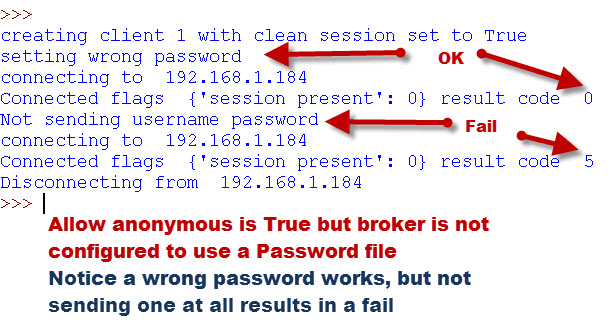
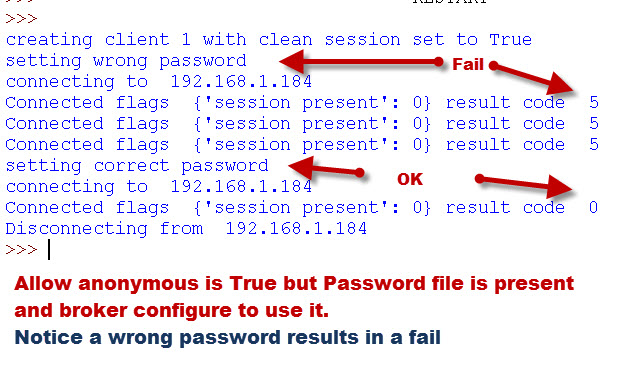
However the Password File is used (if present) ,even if the broker is set to allow_anonymous access.
The follow table shows how the anonymous access setting and the password file settings affect client access.
| Anonymous access | Password file Specified | Access Restricted |
| True | No | No |
| True | Yes | Yes See Note 1 |
| False | No | Yes -see Note 2 |
| False | Yes | Yes |
Note1: If a password file is specified then if the client sends a username/password then it must be valid otherwise an authentication error is returned.
If it doesn’t send one then none is required and a normal connection results.
Note 2: The client must send a Username and password, but it is not checked. If the client doesn’t send a username/password then an authentication error code is generated.
The following examples illustrate these two examples:
In this example we connect to a broker that allows anonymous access but is configured to use the password file.
You can see that if the client supplies a username/password then it is checked.
In this example we connect to a broker that allows anonymous access and is not configured to use the password file.
You can see that if the client supplies a username and password then it works even if they are invalid.However if it doesn’t supply the username/password then the connection fails..
Video
I have created a video that covers the main point above.
Common Questions and Answers
Q- Can I use the same username and password on multiple clients?
A– Yes you can
Q- Is the username and password encrypted?
A– No not unless you are also using SSL on the connection
Q- Can I configure Mosquitto to use authentication on some ports and not others?
A- Yes since v1.5 Mosquitto supports authentication on a per listener basis but it must first be enabled.
Mosquitto v2-Mosquitto_ctrl
The Mosquitto_ctrl tool was introduced with mosquitto v2 and is used for dynamically making user and ACL changes on a mosquitto broker.
It effective replaces the password and ACL file and settings but is not enabled by default and is only likely to be used when an organisation has a large collection of brokers with many frequent changes. Using the Mosquitto_ctrl Tool
Summary
Username and password authentication is common on all computer systems and the Mosquitto MQTT broker supports this authentication mechanism.
To use Password authentication you need to configure the MQTT broker to require it.
The username and password are sent in clear text, and you will need to use TLS to secure it.
It can be configured as a global setting affecting all listeners or on a per listener basis.
Demo Code
Here is the python code that I used to create these examples.
Mosquitto Configuration Tutorials
- Installing The Mosquitto broker on Windows and Linux
- Configuring and Testing MQTT Topic Restrictions
- Configuring Logging on Mosquitto
- Mosquitto MQTT Bridge -Usage and Configuration
- Mosquitto SSL ConFiguration – MQTT TLS Security
- Understanding and Using the Mosquitto Dynamic Security Plugin
Other Related Articles and Resources:
- MQTT for Beginners
- Using the Paho MQTT client for beginners
- Beginners Guide to MQTT Security Mechanisms


hi , when i try to run “mosquitto_passwd -U passwordfile” in cmd, it gives the “Error: Corrupt password file at line 3.”.I created the password.txt and I wrote the path of my txt file instead of “passwordfile”.
HI
if you use the ask steve page to contact me then you can email me the file.
Rgds
Steve
Hi Steve.
I don’t agree with :
“Note 2: The client must send a Username and password, but it is not checked. If the client doesn’t send a username/password then an authentication error code is generated.”
In my case; the connection is refused even providing -u xxx and -P xxx argument to the command.
Are the other condition fulfilled as per the table?
Rgds
Steve
Hi Steve,
Thanks for your guide! I am currently using the javascript MQTT client (for websockets) with SSL and username/password auth on my website. The clients are all connecting using a shared username/password. The only problem is that the usr/pass are stored in the javascript, so the usr/pass can be found in the browser’s inspector, and anyone who gets a hold of that can publish/subscribe to my broker which I don’t want.
Is there any way to make this more secure? Would I need to connect with per user credentials and restrict topic access with ACL? (Or would I need to switch to a PHP or Python client if I do not want to create a user/pass for every user?)
Thanks!!
Hi
Why not get them to enter it manually and then you don’t have to store them.
Rgds
Steve
Hello.
For my MQTT broker I built on my NAS server I purchased domain and DV certificate.
From Cert I received:
certificate.crt,
private key (In text form)
Certificate chain (ROOT/Intermediate CA) (In text form)
CSR (In text form)
also 3 files:
root_ca_1.ca-bundle
root_ca_2.ca-bundle
root_ca_3.ca-bundle
How can I use them in my Mosquitto broker to have tls protection.
Which files I should assign to mosquitto.conf lines:
cafile
keyfile
certfile
Please help.
You use
the ca,the server cert and server key.
Not sure about the bundle on the broker. If you use the ask-steve page to contact me and then email me the files I don’t mind testing them.
Rgds
Steve
Steve,
I’ve been using mosquito quite nicely for the past year, and dynamically adding users with passwords, including the pkill command (as my comment way above mentioned). I do this via a node-red web interface, and then a unix call to add a mosquito user.
Anyway, we are having issues when some web sites add their user credentials via an Access Point mode of our ESP-32 chip (a local wifi and webpage). Sometimes something must sneek into the characters and then the user cannot subscribe. It seems some browsers don’t play nice.
My question to you is if you know how to get mosquito to find out who is attempting this?
The mosquito log in verbose mode only shows:
2022-09-12T16:46:54: New connection from 100.31.206.139:59436 on port 1883.
2022-09-12T16:46:54: Client disconnected, not authorised.
When a valid user tries either the wrong password, or the wrong username (but the correct mosquito host/port).
I really thought a verbose mode would provide the username and password that are being attempted.
Do you know of any way I can find out that information? Is there a $SYS that would let me see dynamic subscription attempts?
thanks,
scott
There is a $SYS topic that lets you see subscriptions but don’t think it will help as you aren’t connected.
It seems that a successful connection attempt shows the username on the broker console but a failed attempt doesn’t.
Rgds
Steve
Hi Scott,
exactly the same challenge here. Have you ever tackled that?
Thanks and best regards
Keith
Hi Steve,
I followed all your instructions, but I am still facing an issue.
1) If I keep “allow_anonymous true” but did not provide the password file path, then I can Subscribe and also receive message from publish.
But when I add the password file path and change “allow_anonymous true” to “allow_anonymous false”
I keep getting Connection refused error.
This is what I enter : mosquitto_sub -t testTopic -h -u -P
This is what I get : Error: Connection refused
2)Does the default.conf also need these commands or should that file remain blank?
I dont have this issue on my Raspberry Pi but cant use it on my Ubuntu OS (Dual Boot).
Thanks in advance.
If you set allow anonymous to false then you need a username/password.
The default conf file is the one used when you let mosquitto start as a service.
When testing I always start mosquitto manually and move the conf file to the /etc/mosquitto/mosquitto.conf file when finished.
use
mosquitto -c password.conf
to start mosquitto where password.conf is you test conf file and place the passwords file in the same folder and again move it later when done.
does that help.
Rgds
Steve
Hey Steve, sorry for replying so late.
I was creating the correct password file but was defining it in default.conf instead of mosquitto.conf
I updated my OS and did the entire process again and its working now.
Thanks.
Starting with the release of Mosquitto version 2.0.0 the default config will only bind to localhost!
If you want to be able to access the broker from other machines you will need to explicitly edit the config files to either add a new listener that binds to the external IP address (or 0.0.0.0) or add a bind entry for the default listener.
You will need to add the following into your mosquitto.conf file
listener 1883 0.0.0.0 ( this will allow access from remote clients)
allow_anonymous true
Cheers
hello steve i create a password file using your instructions now please tell me that should edit orignal config file or crate another config file and how i will test if succesfully password authentication is applied because when i run file you attached in this code so it will connect to the broker and thrn disconnect it not ask me to enter user name and password please help me to resolved this issue
thanks
regards
mohammad
I always use a test config file and no the original one.
You test it by simply setting the username/password to one that is invalid and it should get an auth error.
If you can see the broker console you should see the username being used.
Rgds
Steve
Hi Steve I am confused I created password file and also change the conf file now when I test your script it’s connected with broker now what changes I made in password file so it will give connection error
Thanks and best regards
Mohammad
What is the error and where?Are you seeing it on the client or broker?
Rgds
Steve
Hello Steve I use Mqtt exploler to test I generated password file and change config file but when I try to connect it will connect without user name and password as previously connected please tell me how I resolved this issue
Can you show me the config file
In config file
Per listener settings is true
Allow_annonymus false
Password file file path
But I will not reload config file
May be this is the issue?
Password file file path
is there a real path?
Every time you make a change to the config file you should restart mosquitto.
rgds
Steve
I tried publishing and subscribing to test.mosquitto.org port 1883 “with” the default username and password authentication. Messages can get through. I then tried publishing and subscribing to test.mosquitto.org port 1884 “without” the default username and password authentication. Messages can also get through. I tried rw/readwrite, ro/readonly and wo/writeonly as the username and password. All messages can get through no matter what. What is happening? Am I missing something?
I can only assume that it is allowing anonymous users. There is a note somewhere on the site not to rely on these test brokers.
The best way to test is to install your own broker.
rgds
steve
Dear Mr. Steve
First of all, many thanks regarding your tutorials and videos.
Above you state:
Q- Is the username and password encrypted?
A– No not unless you are also using SSL on the connection
I configured mosquitto.conf to use only port 8883 and tlsv2. Also I passed a file with pairs of user and passwords after running mosquitto_passw. The password became encrypted.
Then I ran the following command on a different machine than the broker :
mosquitto_pub -d -h 192.168.1.145 -u reader -P 456789 -p 8883 -t temperature -m 14 –tls-version tlsv1.2
The broker receives the msg.
Using wireshark I’m able to see the packets and I can see the user and password in plain text.
Do you know how can I encrypt password so that it cannot be seen on the network.
Thanks in advance.
BR
Manuel
Hi
It looks like the –cafile option is missing in the publish
rgds
steve
Steve, thanks for the info.
I’ve been meaning to implement this for dynamically adding new users, and your approach works.
My “add new user” approach is to have a shell script that will run the mosquitto_passwrd tool on the new user, and then append to the ACL file to define the topics allowed for that user.
Then your magic “pkill -HUP mosquitto” does cause it to re-read the config files (password, and ACL). (after 40+ years, I just found the pkill unix command. I’ve always grep, pipe, exec to do it:-)
This can then be done via a node-red “exec” node.
Thanks.
HI, thanks for your posts.
What is best solution to acl and authentication with an sql data base in your opinion?
Hi
I haven’t really researched this but there is a old plugin available that is no longer being worked on. I’m not sure if any more will follow.
https://github.com/jpmens/mosquitto-auth-plug
Cannot make it work. Any configuration I use it always gives me error 5: “Connection refused: Not authorized”
Can you post your conf file.Are you on windows or linux?
Steve – Have you been successful in accessing mosquitto running on Windows from a client not on the same machine? I have followed all of the advice on installing mosquitto on Windows (including the password file, password encryption, and mosquitto_conf file changes) and can never get it to connect with clients on a different machine within the same subnet. I can get node-red running on the same machine to connect with no issue.
I have opened port 1883 on my firewall, in fact tried turning the firewall off, with no change. I have tried accessing mosquitto numerous times both from another PC (running mqtt explorer) and from an esp32 (programmed with the Arduino isp) with no luck.
I was running the current version of mosquitto, but also then tried older versions but with no change.
Have you been successful in connecting to mosquitto running on Windows from other machines, and if so can you tell me what clients you were using and share the code you used with them. Thanks!
Hi
You need a config file with two settings on mosquitto v2
listener 1883
allow_anonymous true
the listener 1883 setting is what allows you access from another machine. See
http://www.steves-internet-guide.com/mosquitto-broker/
at the top
rgds
steve
Hi, Steve
I have a question.
What is the function of `per_listener_settings `? And what is the `listener` meaning?
Since if I donot set `per_listener_settings TRUE`, even I set `allow anonymous FALSE`, I can still connect my broker without username/password. So I really want to know the function of `per_listener_settings `.
Sorry about my English.
Best
mosquitto can listen on multiple ports. So if it is listening on port 1883 and 1884 and using the old version of mosquitto which didn’t have the per listener setting then if allow anonymous was set to False it would affect clients connecting to port 1883 and 1884.
Now with per_listener set to True you can have allow anonymous for clients connected to 1883 and authentication on 1884
Does that make sense?
Rgds
Steve
Good day, and firstly thanks for a very informative article.
I do have a question, more related to ACL.
I have created 2 users both with relevant passwords in the Password file, and in ACL-file listed user1 to be able to subscribe and publish to eg machine/#
user2 I would only like to sub to machine/#
In a nutshell, let’s say there is a switch on machine/switch1 then both user1 and user2 will be able to see the state of switch1. But the intention is for user1 to be able to control the switch, while user 2 will only be able to view the state changes.
I have as example in acl_file the following:
user user1
topic machine/#
user user2
topic read machine/#
Yet with both user password in file and acl, user2 can still also change the state of eg switch1
Can you post the complete ACL file. I tried the ACL file you posted and it works as expected so something must be overriding it.
rgds
Steve
Apologies, I see while the reply await approval, all the items in the text has lost its returns to next line.
config file:
allow_anonymous false
password_file /etc/mosquitto/passwd
acl_file /etc/mosquitto/aclfile
listener 1884
acl file:
# This affects access control for clients with no username. topic read $SYS/#
user reader
topic read @E07C0E5B/#
user @E07C0E5B
topic @E07C0E5B/#
# This affects all clients. pattern write $SYS/broker/connection/%c/state
Thanks you for the response.
Have you tested with a simple config file.
allow_anonymous true
listener 1884
When testing security always do on step at a time so if that works test username/password and after that acl.
you can test acl without passwords by commented out the password file but still send the username/password.
rgds
steve
Thank you so much Steve,
I will revert to a fresh setup, basic config, like in your reply, and then add the acl file with single user first with read only access and test. from there replace that user with user2 for readwrite, and then both.
Just a question re the first and last line on the acl file:
“topic read $SYS/#”
and
“pattern write $SYS/broker/connection.%c/state”
These lines do not have relevance on the issue at hand in the manner it is currently structured?
regards
Riaan
Hi
the “topic read $SYS/#” should be ok.
Not sure about the “pattern write $SYS/broker/connection.%c/state” would need to check that so leave it out for the time being
Thanks you so much for taking the time and having the patience with us newbies on the web.
Managed to get it working correctly, by starting over and following a step by step approach like you suggested starting with allow_anonymous , and adding users, password file, acl etc in small steps.
Thanks again for a great site.
No problem. Good work.
Rgds
Steve
Hi Steve,
Thanks for the great article. Also, your post above helped me. Just want to share my experience, maybe it’ll help somebody else.
I’m working on setting up my own mosquitto broker from the docker container. I started it and first I tried to allow anonymous access and test connection (everything step-by-step).
So, I only uncommented allow_anonymous line and set it to true:
allow_anonymous true
Restarted docker container and got output: Opening ipv4 listen socket on port 1883
So, I decided that it listening on 1883, but my attempt to connect to it failed (I use MQTT Explorer app).
Then I found your post above and uncommented also listener line:
listener 1883
Restarted container and now it works.
This is frustrating because in the config file it is stated “By default, mosquitto will listen on all interfaces”. Obviously, I didn’t understand it. I thought that it’ll be listening on “standard” 1883 port by default. But it doesn’t.
“mosquiito.conf” -> “mosquitto.conf” 😉
tks
Hello Steve,
Does a client get a signal when user credentials is deleted from the broker and the client was already connected to the broker using the same user?
Thanks,
Kavitha.
No It will just not be able to reconnect
Rgds
Steve
Hi steve, can i have a different user name and pass for every user with a special topic? for example 1000 username , pass and topic
Yes you can use the acl to restrict access to the topic
rgds
steve
Thanks Mr.steve.
How do I can prevent duplicate login user with the same username?
In the current state, each client try to connect again and it is bad
Hi
There is nothing to stop clients using the same username and password
Rgds
Steve
Hi
How many users I can add to password_file?
Thanks
I don’t know of a limit
not aware of a limit
Hi Steve,
Want to set up another listener with username / pw authentication (8884). Using systemctl, it fails.
Running manually, the same. Curious if you know why this is puking:
pi@digest:~$ cat /etc/mosquitto/mosquitto.conf
# Place your local configuration in /etc/mosquitto/conf.d/
#
# A full description of the configuration file is at
# /usr/share/doc/mosquitto/examples/mosquitto.conf.example
#
per_listener_settings true
pid_file /var/run/mosquitto.pid
listener 1883
persistence true
persistence_location /var/lib/mosquitto/
log_dest file /var/log/mosquitto/mosquitto.log
listener 1884
allow_anonymous false
password_file /etc/mosquitto/passwords
listener 8883
cafile /etc/mosquitto/ca_certificates/ca.crt
keyfile /etc/mosquitto/certs/server.key
certfile /etc/mosquitto/certs/server.crt
require_certificate true
use_identity_as_username true
tls_version tlsv1.2
log_dest syslog
log_type information
log_timestamp true
include_dir /etc/mosquitto/conf.d
pi@digest:~$ mosquitto -v -c /etc/mosquitto/mosquitto.conf
Error: Unknown configuration variable “per_listener_settings”.
Error found at /etc/mosquitto/mosquitto.conf:7.
Error: Unable to open configuration file.
pi@digest:~$ sudo tail -f /var/log/syslog
Nov 27 22:17:54 digest systemd[1]: mosquitto.service: Failed with result ‘exit-code’.
Nov 27 22:18:04 digest systemd[1]: mosquitto.service: Service hold-off time over, scheduling restart.
Nov 27 22:18:04 digest systemd[1]: mosquitto.service: Scheduled restart job, restart counter is at 33.
Nov 27 22:18:04 digest systemd[1]: Stopped Mosquitto MQTT Broker.
Nov 27 22:18:04 digest systemd[1]: Started Mosquitto MQTT Broker.
Nov 27 22:18:04 digest mosquitto[3851]: Error: Unknown configuration variable “per_listener_settings”.
Nov 27 22:18:04 digest mosquitto[3851]: Error found at /etc/mosquitto/mosquitto.conf:7.
Nov 27 22:18:04 digest mosquitto[3851]: Error: Unable to open configuration file.
Nov 27 22:18:04 digest systemd[1]: mosquitto.service: Main process exited, code=exited, status=3/NOTIMPLEMENTED
Nov 27 22:18:04 digest systemd[1]: mosquitto.service: Failed with result ‘exit-code’.
^C
pi@digest:~$ cat /etc/os-release
NAME=”Ubuntu”
VERSION=”18.04.3 LTS (Bionic Beaver)”
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME=”Ubuntu 18.04.3 LTS”
VERSION_ID=”18.04″
HOME_URL=”https://www.ubuntu.com/”
SUPPORT_URL=”https://help.ubuntu.com/”
BUG_REPORT_URL=”https://bugs.launchpad.net/ubuntu/”
PRIVACY_POLICY_URL=”https://www.ubuntu.com/legal/terms-and-policies/privacy-policy”
VERSION_CODENAME=bionic
UBUNTU_CODENAME=bionic
pi@digest:~$
It coul bde that you need to move these lines out of the listener section
persistence_location /var/lib/mosquitto/
log_dest file /var/log/mosquitto/mosquitto.log
also I would always use a local config file when testing
Stevie-wonder! Ordering was indeed the issue. Thank you so much for your attention 🙂
For future reference, a simplified test config is as follows:
————————————————————————————————-
pid_file /var/run/mosquitto.pid
persistence true
persistence_location /var/lib/mosquitto/
log_dest file /var/log/mosquitto/mosquitto.log
per_listener_settings true
listener 1883
listener 1884
allow_anonymous false
password_file /etc/mosquitto/passwords
log_dest syslog
log_type information
log_timestamp true
include_dir /etc/mosquitto/conf.d
————————————————————————————————-
Thanks again!
Hi steve,
I tried the username password authentication but it doesnt seem to work.I am able to publish even if i have entered a wrong username password.My config file includes only allow_authentication false and my passwords file has username and encrypted passwords.I have reloaded the mosquitto.conf file .Where do you think i am going wrong?
Hi
It should be allow_anonymous false
rgds
Steve
sorry that was a typo..i included allow_anonymous.
Are you sure that you a picking up the conf file what command are you using to start mosquitto and wher eis you conf file located? Are you on windows or linux.
I am using linux.config file is in the location /etc/mosquitto .I use mosquitto -v to start mosquitto.Each time i edit the config file i run the mosquitto -c path_to_config file and then reboot.How do i make sure that its picking up the correct config.I had checked it making an mistake in the config file. mosquitto -v /mosquitto -c path_to_config wouldnt work.
Hi steve,
Thanku soo much..The questions you asked me really helped me. i was initially using mosquitto -v /mosquitto to start the mosquitto. I tried with sudo service mosquitto start and it works perfectly now !!
Regards,
smitha.
Hi Steve, I did the set up of a mosquitto broker on a VPS, with access to one user and works well while in the VPS, if I try to connect from another computer I get no response, a timeout or no route to host message. I am guessing a DNS issue, but wanted to know if you have encountered a similar problem when trying to connect to a Mosquitto instance in a VPS from other devices. Thanks
I would suspect that the ports are being blocked. I did a setup on an Amazon server instance and found they were all blocked by default.
Rgds
Steve
Hi, was very useful, can we also restrict number of connections per username
No only the total number of connections
rgds
steve
how do you suggest we can do this in application layer, or we can’t do it at all? Because I have seen cloudmqtt has this feature
Cloudmqtt use a different mosquitto instance as far as I can tell but I will look at it again
rgds
steve
thank you steve for the quick correspondence
Hi Steve,
I use username and password authentication in Mosquitto
When i receive new published message,Can i know who username publish message?
Example does Jack publish message or Rack
Thanks
Hi
You can’t unless you include that information in the actual message.
rgds
steve
As a result,finally i have to use SSL for high security
Thanks
Hi Steve, I would like to include a picture to my Node-Red Dashboard that subscribes to Mosquitto MQTT topics that currently shows Temperature and Humidity of the room the microcontroller is installed.
For that I addapted a script that can be found at: https://github.com/ldab/ESP32-CAM-MQTT to use Mosquitto instead of cloudmqtt.com/
There are instructions to increase buffer size at PubSubClient.h as below:
#define MQTT_MAX_PACKET_SIZE 1530
But it has no effect at all for my problem.
I have verified on the debug code on the link below that it prints the image buffer (in Hex) successfully at the Serial monitor of the microcontroller.
I have also verified using WIRESHARK at the Ubuntu/Mosquitto server that only the first 8 bytes “FFD8FFE0” of the image taken do arrive to Mosquitto. I also found that this 8 bytes heading indicates it is a JPG image.
Now I am trying to find out if the rest of the image (more than 2Kbytes in most cases) is lost at the ESP32CAM side or just ignored by Mosquitto for some buffering limitations.
The printout of the debug and sketch are large and to avoid polluting your page I provide the link in case you have the time to take a look on it:
https://esp32.com/viewtopic.php?f=22&t=12326&p=49291#p49291
Any assistance welcome.
Thanks
Hi
I haven’t done much with arduino and C but I did get a pub/sub script running on arduino a while back and seem to remember a buffer limit of 128 bytes.
I would assume that you would need to loop thought he image file sending 100bytes each time and then reassemble it at the other end.
I did a similar thing with python
http://www.steves-internet-guide.com/send-file-mqtt/
As a matter of interest couldn’t you just send the temperature value rather than an image
Rgds
Steve
Dear Steve, thanks for your prompt response.
I will investigate the link you provided.
If nothing works sending the image in small pieces may be the solution.
The reasons I want to send the picture as well is that it provides for a view of the environment on the room where the sensors are and second, it is a comercial solution and it looks nicer to have an overview of what is going on.
Thanks again for your time
Regards
Paulo
i have entered my username and password to connect to the broker for lohin,even thought i entered the wrong password and username i am logging in .tell mi solution
Hi
Check that you have set allow anonymous to false
rgds
steve
Hi Steve,
1) I have followed your instructions and created a password.txt file
cat /etc/mosquitto/conf.d/passwords.txt
will display the long encrypted password
2) I have found two mosquito.conf files on my system ( mosquitto is running on a QNAP in Container Station )
find -name “mosquitto.conf” -print
./etc/init/mosquitto.conf
./etc/mosquitto/mosquitto.conf
3) I have added two lines in both mosquito.conf files
allow_anonymous false
password_file /etc/mosquitto/conf.d/passwords.txt
4) I stopped and restarted my mosquito app
PROBLEM :
No difference
I am still able to connect and publish anonymously (I am using MQTT.fx)
Any idea ?
Thanks for reading my comment,
Regards
Eric
I would suspect that it isn’t picking up the conf file. Put an error in the file e.g
allowanon false
and see if it shows when you try starting.
alternatively load it from the command line
mosquitto -c conffile
let me know what happens and use the ask steve page to send me the file
Rgds
Steve
How we can implement authentication to secure mqtt connection between client and server (say, nodemcu and raspberry)? and is it possible to implement without using third party cloudmqtt servers
What mqtt broker are you using. If it is mosquitto then it supports basic authentication.
Rgds
Steve
I’m using mosquitto and how can I achieve the authentication in the local network?
Best,
Vijay
It is covered in the tutorial. AM I missing something?
Rgds
Steve
Hi steve,
I am using Mainflux – 3rd party IoT platform. I want to connect the paho mqtt client to the mainflux. Mainflux accepts token based authorization. How to pass the authorization token in the client.connect command?
According to the github page it is sent as the password
To use MQTT adapter you should use channels//messages. Client key should be passed as user’s password. If you want to use MQTT over WebSocket, you could use Paho client:
Rgds
Steve
There’s another authentication method using JWT (https://www.groundai.com/project/json-web-token-jwt-based-client-authentication-in-message-queuing-telemetry-transport-mqtt/1) which the Google IoT is also using. How secure is it? Can you please write an article on it covering practical implementation?
Thanks
Tim
Interesting read. One thought. I forgot to mention payload encryption earlier.
If you encrypt the payload and not the connection then you get end to end security.
http://www.steves-internet-guide.com/encrypting-the-mqtt-payload-python-example/
if you combine it with simple username/password authentication then it is very lightweight and easy to implement when compared with the other methods.
Thanks Steve.
But how secure it will be compared to other methods? Thanks
I’m not a security expert but the encryption can be made as secures as SSl so just as secure. There is no verification on Broker so you could be using a none trusted broker but I’m not sure that is a problem as the message is encrypted.
IMO the security solutions being proposed are based on web systems were the interaction is client server. MQTT is client-server-client and possibly more. It is more like email than the web.
Hi Steve,
Can we use databases for the authentication and is that necessary to restart config files after adding new users ?
Yes there are plugin options but you need to write the code. I haven’t tried that or seen it done.
When using the text file for passwords you need to get the broker to reread it after any changes.
rgds
steve
thanks
Nice write up Steve!
I was wondering if I run the kill-HUP PID command will it stop the broker from receiving messages or only reloads the config file?
Only reloads the config file
In MQTT V5.0 just released, there’s an AUTH control message newly introduced. How does this impact current implementations? Can the new control message be used to simplify authentication? Thx
It doesn’t really impact current implementations as they don’t use it and existing authentication mechanisms have been retained.
I don’t think it will simplify authentication as it is pretty simple as it stands.
It is meant to be used to create more sophisticated authentication schemes. See this Hive article
https://www.hivemq.com/blog/mqtt-5-foundational-changes-in-the-protocol/