How Does MQTT Work ?-MQTT is a messaging protocol i.e it was designed for transferring messages, and uses a publish and subscribe model.
This model makes it possible to send messages to 0,1 or multiple clients.
A useful analogy is TV or radio.
A TV broadcaster broadcasts a TV program using a specific channel and a viewer tunes into this channel to view the broadcast.
There is no direct connection between the broadcaster and the viewer.
In MQTT a publisher publishes messages on a topic and a subscriber must subscribe to that topic to view the message.
MQTT requires the use of a central Broker as shown in the diagram below:
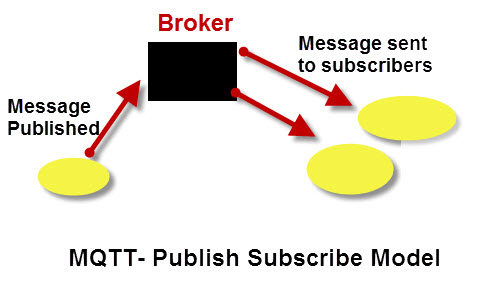
Important Points to Note
- Clients do not have addresses like in email systems, and messages are not sent to clients.
- Messages are published to a broker on a topic.
- The job of an MQTT broker is to filter messages based on topic, and then distribute them to subscribers.
- A client can receive these messages by subscribing to that topic on the same broker
- There is no direct connection between a publisher and subscriber.
- All clients can publish (broadcast) and subscribe (receive).
- MQTT brokers do not normally store messages.
Introductory MQTT Video
This video takes you through the basics of MQTT.
MQTT Client-Broker Connections
MQTT uses TCP/IP to connect to the broker.
TCP is a connection orientated protocol with error correction and guarantees that packets are received in order.
You can consider a TCP/IP connection to be similar to a telephone connection.
Once a telephone connection is established you can talk over it until one party hangs up.
Most MQTT clients will connect to the broker and remain connected even if they aren’t sending data.
Connections are acknowledged by the broker using a Connection acknowledgement message.
You cannot publish or subscribe unless you are connected.
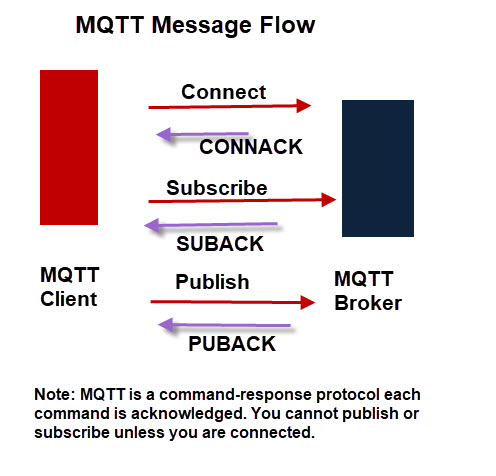
MQTT clients publish a keepalive message at regular intervals (usually 60 seconds) which tells the broker that the client is still connected.
See MQTT Keep Alive Interval Explained
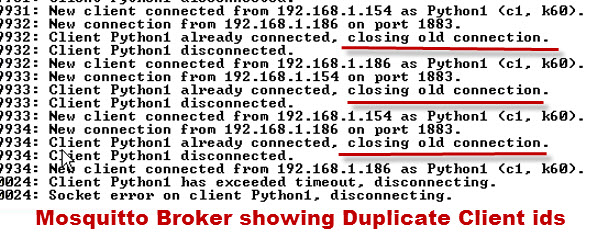
The Client Name or Client ID
All clients are required to have a client name or ID.
The client name is used by the MQTT broker to track subscriptions etc.
Client names must also be unique.
If you attempt to connect to an MQTT broker with the same name as an existing client then the existing client connection is dropped.
Because most MQTT clients will attempt to reconnect following a disconnect this can result in a loop of disconnect and connect.
The screen shot below show what happens when I try and connect a client to the broker using the same client id as an existing connected client.
Clean Sessions
MQTT clients by default establish a clean session with a broker.
A clean session is one in which the broker isn’t expected to remember anything about the client when it disconnects.
With a non clean session the broker will remember client subscriptions and may hold undelivered messages for the client.
However this depends on the Quality of service used when subscribing to topics, and the quality of service used when publishing to those topics.
Understanding Clean sessions Video
Last Will Messages
The idea of the last will message is to notify a subscriber that the publisher is unavailable due to network outage.
The last will message is set by the publishing client, and is set on a per topic basis which means that each topic can have its own last will message.
This means that each topic can have its own last will message associated with it.
The message is stored on the broker and sent to any subscribing client (to that topic) if the connection to the publisher fails.
If the publisher disconnects normally the last Will Message is not sent.
The actual will messages is including with the connect request message.
See Last Will and Testament example using Python
Python Client Example
This tutorial takes you though creating a client connection using the Paho MQTT client.
It looks at successful and failed connections and how to deal with them. – Working with Client Connections
Next ==> MQTT Topics and Topic Structure
Resources:

Hi Steve,
what do you mean when said “The job of an MQTT broker is to filter messages based on topic, and then distribute them to subscribers”.
You mean the broker determines who is subscribe to which topic and send them to those subscribers.
Also, “All clients can publish (broadcast) and subscribe (receive)”. I thought all clients are connected to a broker “unicast address” When you said broadcast – you don’t mean all “255.255.255.255”. Thx
Hi
Broadcast in this sense is send to multiple subscribers. MQTT works like radio and TV. The station broadcasts a program which can be viewed/heard by many listeners/viewers.
However they need to tune into that broadcast or in the case of MQTT subscribe to that topic.
Does that make sense?
Rgds
Steve
I need to know if something is possible like
a) 10 clients have subscribed to mqtt topic
b) publisher publish the message
c) I want out of 10 only 4 clients should receive the message and remaining 6 shouldn’t receive the message
Is something like this is possible, if yes please provide your inputs.
In MQTTv5 you can do load sharing but I don’t think that is what you want as I assume you want to designate which clients receive it.
If only 4 are to receive it why do the others need to subscribe.
Rgds
Steve
Thanks for the tutorial(s). As far I understood that the clients do not have any unique ID (only local unique) nor fixed IP, and the Broker preferably with a fixed IP address. Is my understanding correct? If so, is there any way to globally identify a client? I mean suppose combining client ID and Broker-ID/IP-address etc.? Is there any standard way or better way?
Regards,
Deb
Your understanding is correct. The client id is fixed when clean sessions is false. However the client id isn’t known by the receiving client.
The way I do it is adding the client id to the topic. You may find this tutorial of interest
http://www.steves-internet-guide.com/two-way-communication-mqtt-python/
rgds
steve
Thank you for this tutorial.
Hi Steve, say you want to design two separate setups (each setup has many pub and sub clients and different topics) and they both use the mosquito broker in one server station, do you have to create different userbnames and passwords for each of the setups otherwise how do you stup them from interfering?
Hi
Providing they use different topics they don’t interfere with each other. You could also restrict topic access using Access control lists on Mosquitto to make sure they they could accidentally interfere with each other.
http://www.steves-internet-guide.com/topic-restriction-mosquitto-configuration/
rgds
Steve
hi im not able to connect my dut mqtt client with broker. do i need to add ipadress of client in broker somewhere?
No you just meed to add the ip address of the broker to the client. Is it your own broker?
hey,is it possible to replace tcp/ip stack with ndn based packet delivery
Hi
I doubt it.I’ve never heard of it.
Rgds
Steve
Hello Steve, is it possible to view the payload data from the Publisher in the broker(mosquito)?
No it only shows the number of characters.
rgds
steve
I mean invalid password as per you article http://www.steves-internet-guide.com/mqtt-username-password-example/.
Thanks
Sorry not quite sure of the question
As you have explained in your article “Mosquitto Username and Password Authentication -Configuration and Testing” in above link that “…if the client supplies a username and password then it works even if they are invalid.”. It means that even if client tries to login with invalid password, it gets the access to broker! Does other Broker also has this drawback like it is in Mosquitto? How can this authentication be made secure then?
That would be implementation dependent as it is not specified.However this is only if anonymous access is enabled
Hi Steve, thanks for great article. In your article you wrote that “If you attempt to connect to an MQTT broker with the same name as an existing client then the existing client connection is dropped.” It is well true. But suppose if I am an attacker and I know the existing clientID of your device and topic your client is publishing at. So if I use the same existing clientID then your device will be disconnected and from this time forward I force my device to publish the false information on the topic. What will happen, the system will generate wrong insight. So is there any way to make a broker refuse the connection if there’s a connection with same clientID is already established. Thanks.
On Mosquitto no. I also think that the MQTT spec specifies that behaviour.
You would need to implement username/password to block the client from sending data
Rgds
Steve
Since multiple clients can use same username and password to login to broker, is there any way to restrict a client to use only one username/password?
Not as far as know on Mosquitto but it might be possible on other brokers
Thanks steve, and what about login with wrong password? Like Mosquitto, other brokers too have this drawback?
Not sure what you mean regarding wrong password. If anonymous is off then it will fail as expected otherwise the username/password is ignored for authentication but will be taken into account in the ACL.
Rgds
Steve